In NS Module 4, we learnt about the role of the Domain Name System (DNS) in Internet naming and addressing. In this lab exercise, we will go deeper into DNS by using specialised network tools to perform and analyse DNS queries.
At the end of this lab exercise, you should be able to:
- Use
digto perform DNS queries (e.g. to look up an IP address) - Read and interpret DNS records of different types
- Understand how a DNS query is resolved using hierarchy and recursion
- Observe and understand the effect of caching on DNS lookup times
- Use Wireshark to trace and read DNS packets sent to and from a machine
- You can download the installer for macOS/Windows here
- If you use Ubuntu, run the following commands. You can then run wireshark with
sudo wireshark.sudo apt update sudo apt install wireshark
Part 1: Exploring DNS via dig
The Domain Information Groper (dig) is commonly used for performing DNS lookups. Here is an example of how it can be used to find information about the host slashdot.org. The results may differ if you run the same query on your machine.
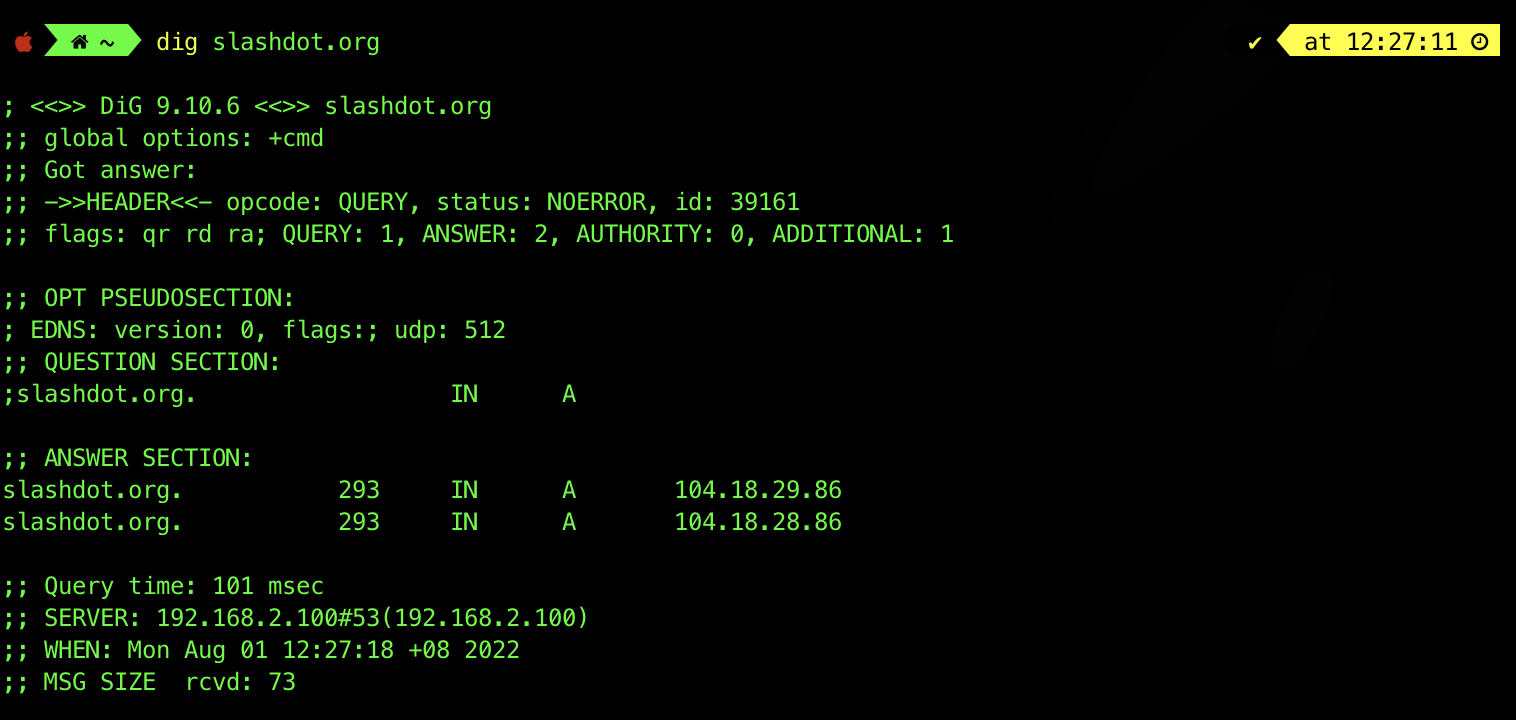
When the command dig slashdot.org is run, dig performs a DNS lookup and displays information about the request and the response it receives. At the bottom of the printout, we can see that the query was sent to the DNS server running on 192.168.2.100, and that the query took 101 ms to complete. Most of the information that we are interested in can be found in the ANSWER SECTION.
The answer section for this query contains a DNS record:
| Server Name | Expiry (TTL in seconds) | Class | Type | Data |
|---|---|---|---|---|
slashdot.org |
7200 | IN | A |
67.251.97.40 |
- We can see that the result is of type
A, an address record. - It tells us that the IP address for the domain name slashdot.org is
67.251.97.40. - The expiry time field indicates that this record is valid for 7200 seconds.
- The value of the class field is usually IN (Internet) for all records.
If you’d like to know who’s the authoritative NS for the queried domain, you can add the trace option: dig slashdot.org +trace
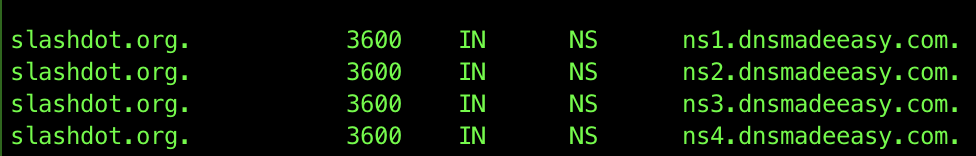
The records of type NS indicate the names of the DNS servers storing records for a particular domain. Here, we can see that the hosts ns1.dnsmadeeasy.com. and etc are responsible for providing authoritative responses to names in the slashdot.org domain.
We can query a specific server for information about a host by using the @ option. For example, to perform a lookup using the DNS server ns1.dnsmadeeasy.com., we can run the command dig @ns1.dnsmadeeasy.com. slashdot.org.:
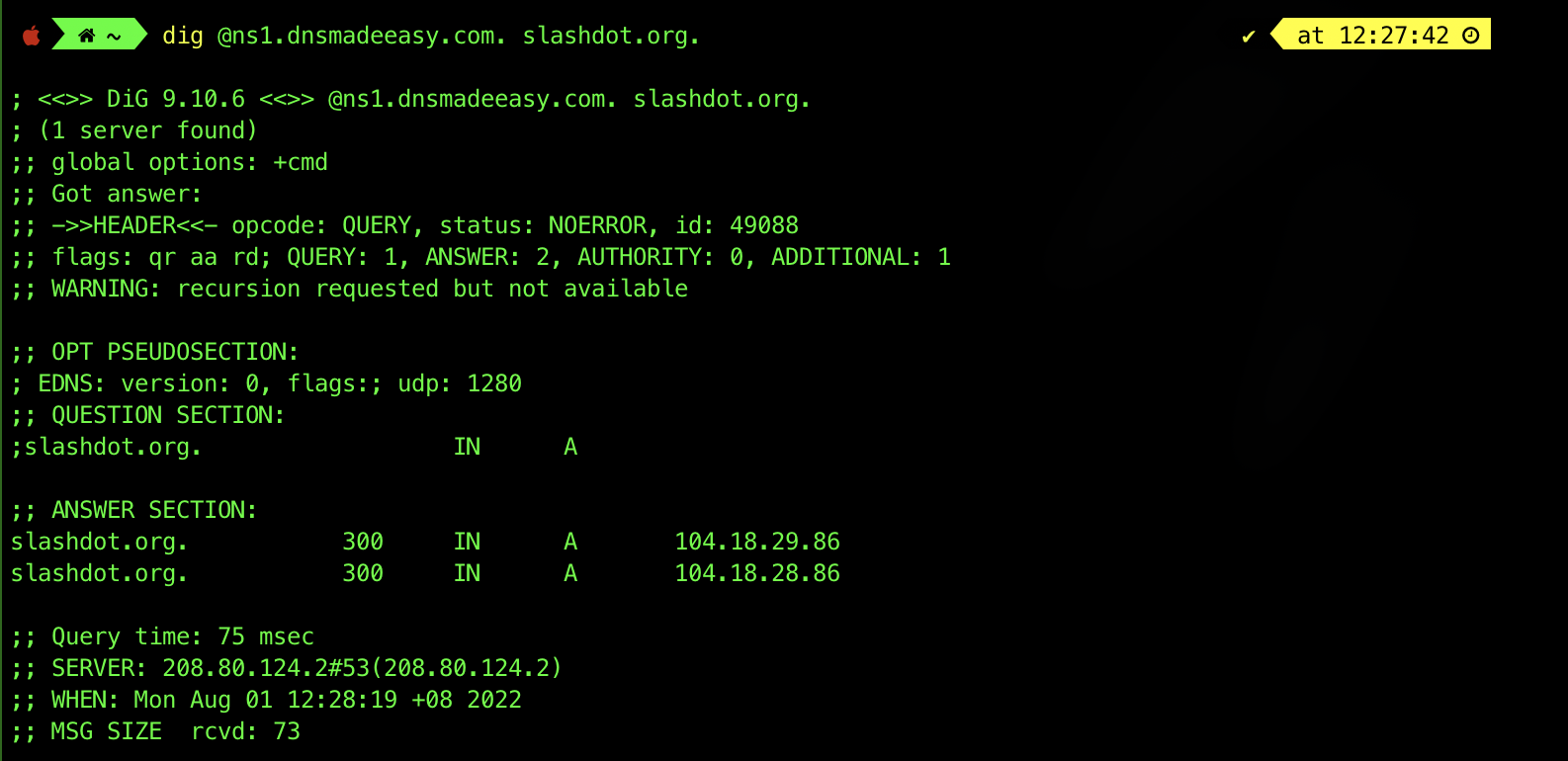
There are three flags under the header: qr, aa, and rd:
- This means that the message is a query (
qr), and dig is requesting a recursive lookup (rdstands for ‘recursion desired’) and the server is the authoritative name server (aastands for ‘authoritative answer’). - Not all servers perform recursive lookups due to the heavier load involved, and so you don’t see any
raflags here (rastands for ‘recursion available’).
dig only prints the final result of a recursive search, but you can mimic the individual steps involved by making a query with the +norecurs option enabled. For example, to send a non-recursive query to one of the root servers, we enter the command dig @a.ROOT-SERVERS.NET www.slashdot.org +norecurs:
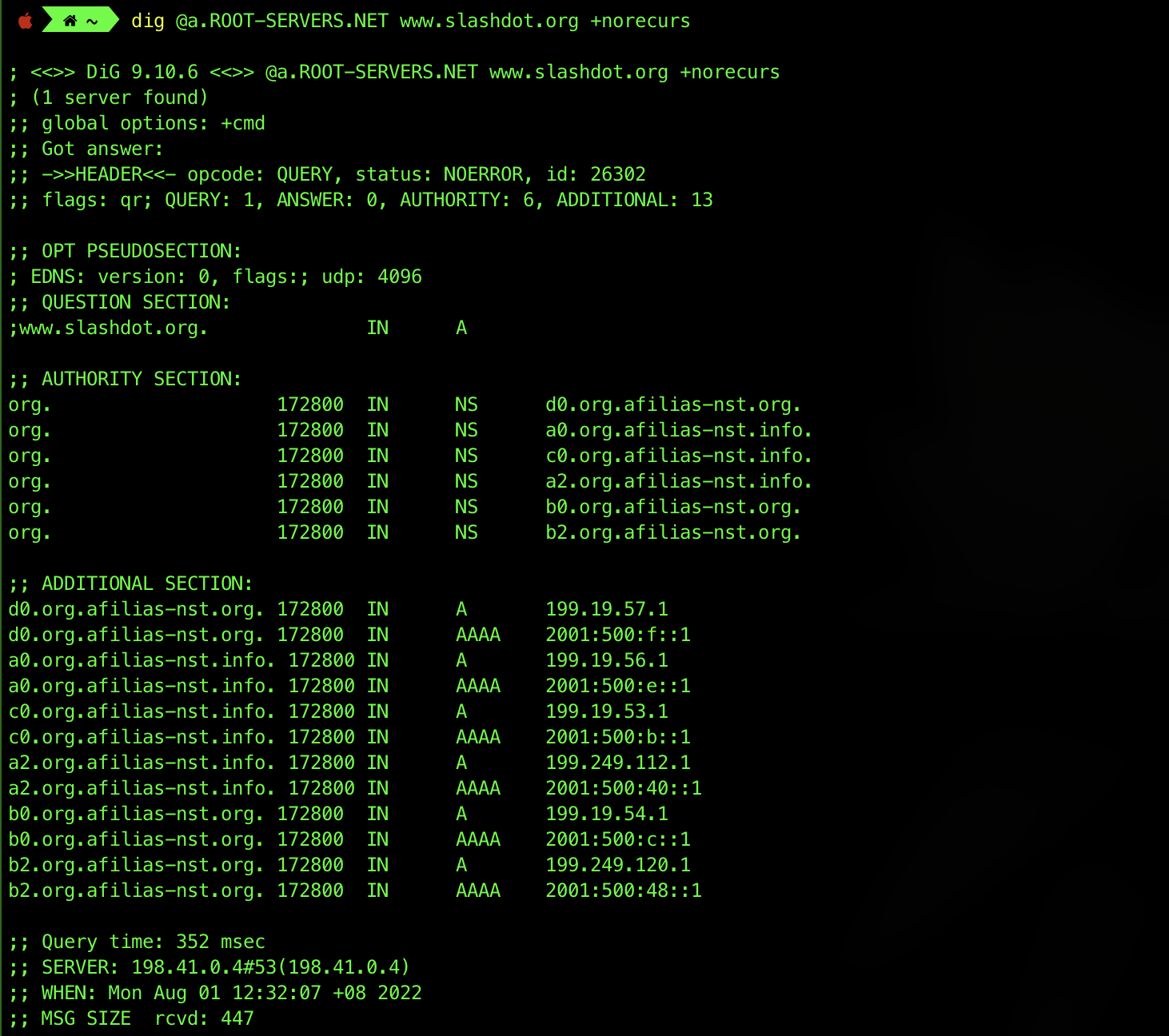
As you can see, the server does not know the answer (there’s 0 ANSWER) and instead provides information about the servers most likely to be able to provide an authoritative answer for the question. In this case, the best that the root server knows is the identities of the servers for the org. top-level domain.
Task 1
TASK 1: Using dig, find the IP address for thyme.lcs.mit.edu. What is the IP address?
Task 2
TASK 2: The dig answer for the previous question includes a record of type CNAME. What does CNAME mean?
Task 3
TASK 3: What is the expiration time for the CNAME record?
Task 4
TASK 4: Run the following commands to find out what your computer receives when it looks up ‘ai’ and ‘ai.’ in the mit.edu domain. What are the two resulting IP addresses?
dig +domain=mit.edu aidig +domain=mit.edu ai.
Task 5
TASK 5: Find out why the results for both queries are different.
Look up the manual for dig to find out what the +domain parameter does. Based on the output of the two commands, what is the difference between the DNS searches being performed for ai and ai.?